Owner of SiegedSec Targets UHG Data in Illicit Telegram Bot🚨
Recent screenshots from a Telegram channel reveal lucid(The Owner of SiegedSec) actively searching for leaked data associated with uhg.com
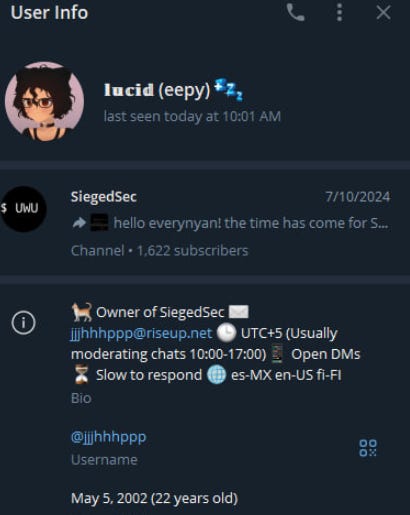
The underground Telegram scene just got messier. The enigmatic lucid (eepy), owner of SiegedSec, is at it again—this time digging into uhg.com data leaks. If you’ve been following the drama, SiegedSec has made waves with hacktivist antics and brazen data breaches, and now lucid’s latest move targets one of the largest healthcare entities in the world.
What’s Going Down?
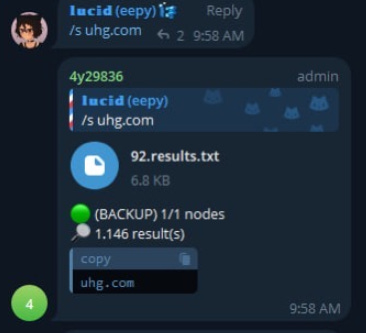
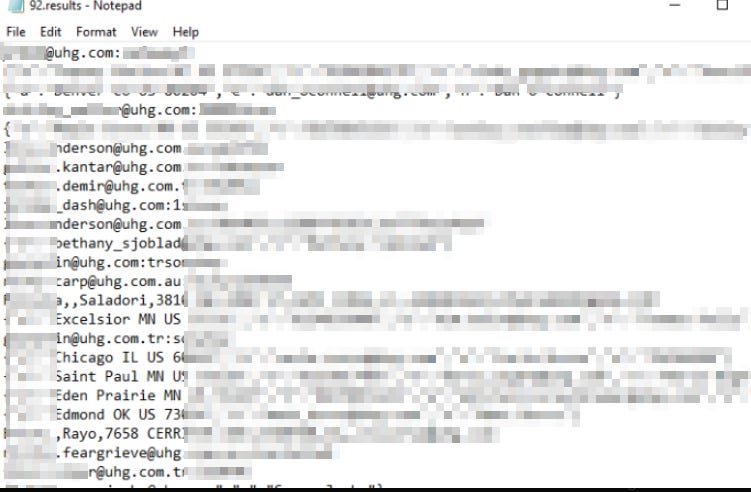
In newly surfaced Telegram screenshots, lucid used an illicit bot to query for “/s uhg.com,” pulling a file labeled 92.results.txt packed with over 1,000 entries of sensitive UHG data. The file contains:
Email addresses, names, and identifiers tied to UHG personnel.
Enough breadcrumbs to open doors for phishing attacks, social engineering, and worse.
But this isn’t just a casual scroll-through-data moment. lucid’s Telegram profile confirms their ownership of SiegedSec, an infamous hacking collective known for its mix of hacktivism and chaos. And, by chaos, we’re talking about taking aim at high-profile targets like the Heritage Foundation and other major players.
SiegedSec 101: Hacktivism Meets Anarchy
If you’re new to SiegedSec, here’s the cheat sheet:
The Heritage Foundation Hit: SiegedSec leaked 2GB of sensitive data from this high-profile think tank, including donor lists and internal files.
Hacktivist Origins: The group claims to target corruption, corporate greed, and authoritarian regimes—often mixing political messaging with their data breaches.
Disbandment Drama: They briefly “shut down” after the Heritage Foundation breach, only to reemerge stronger, with lucid leading the charge.
Now, their focus has shifted toward corporate behemoths like UHG, using Telegram bots and other tools to harvest sensitive data and weaponize it.
Why It Matters
SiegedSec isn’t just some script kiddie group—they’re a rapidly evolving threat actor leveraging:
Automation Tools: Bots to locate and exploit leaked data faster than ever.
Targeted Campaigns: Strategic focus on high-value entities like UHG.
Hacktivist Spin: Their actions are often draped in political messaging, but the consequences are real and devastating.
lucid’s latest activity highlights the alarming ease with which hackers can access sensitive corporate data, turning it into ammunition for phishing campaigns, ransomware, and more.
What’s Next?
UHG and other corporations targeted by SiegedSec need to:
Monitor the Underground: If your data’s showing up on Telegram bots, it’s already too late.
Harden Defenses: Ramp up vulnerability scans and tighten access controls across your systems.
Prepare for Fallout: Phishing campaigns, insider threats, and public embarrassment are just the beginning if this data is weaponized.
The SiegedSec Playbook
SiegedSec’s ability to straddle hacktivism and raw exploitation makes them a unique threat in the cybercrime ecosystem. Whether targeting political organizations or healthcare giants, their tactics are a wake-up call for companies across every sector.