Hikki-Chan: Unmasking a Fraudulent Hacker and The Iranian Connection
Unraveling the Web of Deception: How a Self-Proclaimed Hacker Exploits Geopolitical Tensions with Recycled Data and False Claims
New threat actors frequently emerge, each claiming responsibility for high-profile attacks. Recently, a figure known as "Hikki-Chan" has gained notoriety on hacking forums. However, careful analysis reveals that this supposed hacker may be nothing more than a fraudster attempting to capitalize on current geopolitical tensions. This report aims to dissect Hikki-Chan's claims and expose the reality behind the facade.
The VK Leak: A Cornerstone of Credibility?
Hikki-Chan's reputation largely rests on a purported leak of data from VK (VKontakte), a popular Russian social networking site. However, closer examination suggests that this "leak" consists of scraped public data rather than information obtained through a genuine breach. This pattern of presenting publicly available information as exclusive, stolen data is a common tactic among fraudulent actors seeking to build credibility in hacking communities.
The Kavim Incident: A Case of False Attribution
One of Hikki-Chan's most audacious claims involves the alleged hacking of Kavim, an Israeli public transportation company. However, this incident can be definitively attributed to "Black Shadow," an IRGC-affiliated group that targeted Kavim in 2021.
Bleeping Computer, a respected cybersecurity news outlet, reported on the Black Shadow attack in detail.
Their article, available here, provides a comprehensive breakdown of the actual incident.
Hikki-Chan's attempt to take credit for this well-documented attack raises serious questions about the veracity of their other claims.
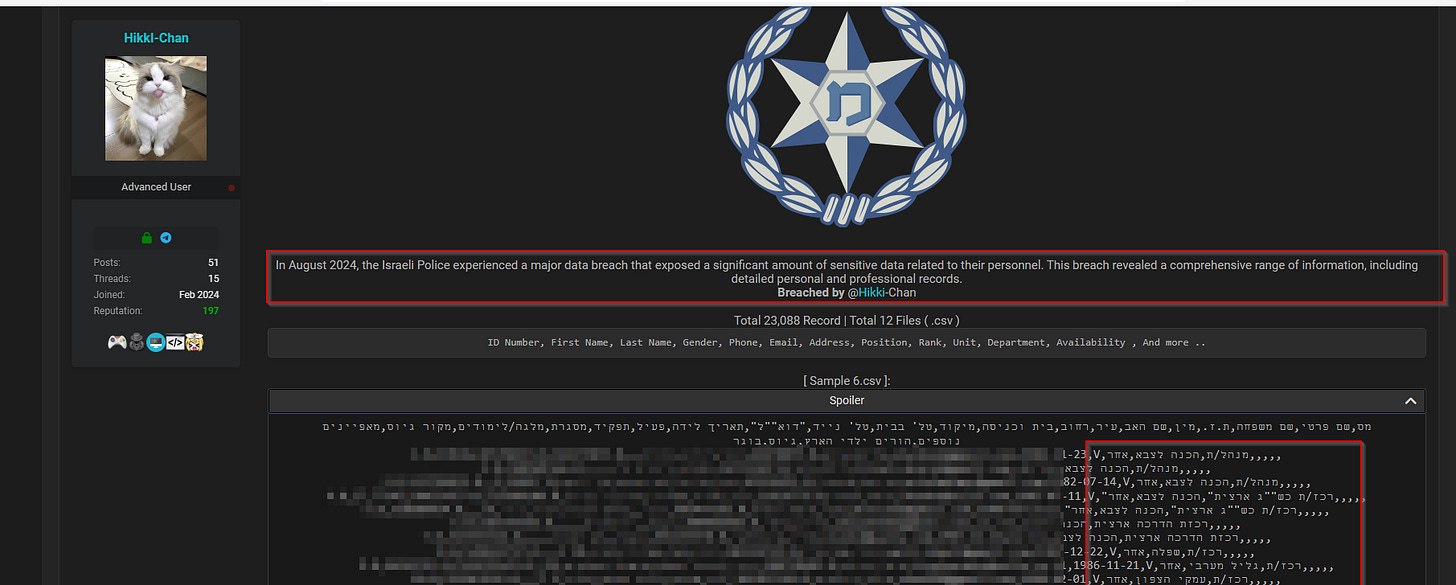
The Israeli Police Database: A Misrepresentation
Another significant claim by Hikki-Chan involves an alleged breach of the Israeli Police database. However, analysis of the data offered reveals that it is unrelated to law enforcement. Instead, the information pertains to "Aharai" (After Me), a youth organization that helps prepare Israeli teenagers for military service.
Moreover, this data isn't new. Research conducted by ClearSky, a cybersecurity intelligence firm, confirms that this exact dataset first appeared on hacking forums in June 2023, months before Hikki-Chan's emergence. This strongly suggests that Hikki-Chan is recycling old, previously leaked data rather than obtaining new information through actual hacking activities.
Thanks to research by ClearSky cyber security analysts, we could provide you with the data mentioned above.
The Iranian Connection
Iranian state-sponsored Advanced Persistent Threat (APT) groups have been observed engaging in sophisticated disinformation campaigns, notably involving the publication of purportedly leaked Israeli databases. This analysis examines the tactics, techniques, and procedures (TTPs) employed in these operations, with a focus on their strategic objectives and potential impact.
Prominent Threat Actors:
Charming Kitten (APT35)
OilRig (APT34)
Primary Tactics:
Dissemination of fabricated or outdated databases
False claims of data exfiltration from Israeli sources
Strategic Objectives:
Generate media attention
Conduct psychological operations
Undermine Israeli reputation and perceived security posture
Operational Patterns:
Release of ostensibly sensitive information, often including personal data
Utilization of social media and dark web forums for distribution
Data Veracity:
Many leaked databases proven to be:
Outdated
Incomplete
Entirely fabricated
These disinformation campaigns represent a nuanced approach to cyber warfare, where the primary objective extends beyond direct system compromise. By creating the illusion of successful cyber intrusions, these APT groups aim to:
Sow confusion among targeted populations
Erode trust in Israeli cybersecurity measures
Compel Israeli security resources to be allocated to threat verification and mitigation
Here are examples of Iranian APT groups publishing fake or outdated Israeli databases as part of their cyber operations:
1. Charming Kitten (APT35) - "Pay2Key" Ransomware Campaign (2020)
In late 2020, the Iranian-linked APT group Charming Kitten (APT35) was believed to be behind the "Pay2Key" ransomware attacks targeting Israeli companies. After some attacks, the group posted what they claimed were stolen databases from Israeli organizations. However, cybersecurity analysts found that some of these leaked databases were either outdated or fabricated, likely aimed at causing panic and reputational damage rather than gaining financial benefit or releasing valuable information.
2. MuddyWater (APT34) - Fake Leaks of Israeli Government Data
MuddyWater (APT34), another Iranian-affiliated group, has been involved in disinformation campaigns where they claim to have breached Israeli networks. In several instances, MuddyWater published what they purported to be sensitive Israeli government or military databases. Investigations into these leaks revealed that some of the data was outdated or tampered with, undermining the credibility of the claims but still creating headlines that served their propaganda goals.
3. Hackers of Sabrin - Fake Israeli Voter Database (2020)
In 2020, an Iranian-affiliated group known as Hackers of Sabrin claimed to have leaked a database of Israeli voters, which they said they obtained from government systems. While parts of the data appeared authentic, much of it was old and incomplete. Analysts concluded that the group’s goal was to incite fear and distrust within the Israeli public rather than to expose current or useful information.
4. Black Shadow - Insurance Data Leak (2021)
The Black Shadow hacking group, believed to have ties to Iran, breached Israeli insurance company Shirbit in 2021. They published personal details of Israeli citizens on the dark web. While some of the leaked data was accurate, many of the published records were old or had already been publicly available, signaling an attempt to cause panic and damage Israel’s reputation.
5. Islamic Revolutionary Guard Corps (IRGC) - Fake Financial Data Leak (2018)
In 2018, an Iranian state-affiliated cyber group, believed to have links to the IRGC, claimed to have breached Israeli banks and financial institutions. They released what they said was sensitive financial information. Upon review, cybersecurity experts determined that much of the data was outdated or fabricated, designed to manipulate the public perception of Israel's cyber vulnerabilities.
These incidents demonstrate how Iranian APTs use the tactic of releasing fake or old databases as part of broader cyber warfare strategies that include disinformation, psychological operations, and propaganda. The goal is often less about the immediate impact of the data and more about shaping narratives and inciting fear.
Huge thanks to Alon Gal The Co-Founder & CTO @ Hudson Rock (Cybercrime intelligence)
Threat Actor Profile Analysis
Based on the available information, we can construct the following profile of Hikki-Chan:
Alias: Hikki-Chan
Forum Reputation: As of the latest check, Hikki-Chan has accumulated 197 reputation points on their primary forum. It's worth noting that this increase in reputation coincides with heightened geopolitical tensions following the events of October 7th, 2023.
Suspected Motivation: While it's challenging to determine precise motivations without direct evidence, the pattern of behavior suggests that Hikki-Chan may be affiliated with or acting as a proxy for state-sponsored actors, possibly the Islamic Revolutionary Guard Corps (IRGC). The primary goal appears to be conducting psychological operations (Psy-Ops) aimed at portraying Israeli cyber defenses as vulnerable.
Modus Operandi: Hikki-Chan's strategy involves:
1. Repurposing old, publicly available data leaks
2. Falsely claiming credit for well-documented attacks by other groups
3. Misrepresenting the nature and origin of the data they claim to have obtained
4. Leveraging current geopolitical tensions to gain credibility and attention
Conclusion
The evidence strongly suggests that Hikki-Chan is not a legitimate threat actor but rather a fraudulent entity engaged in misinformation and reputation-building through deception. Their claims consistently fail to withstand scrutiny, relying on misattributed attacks, recycled data, and misrepresented information.
For cybersecurity professionals and researchers, this case underscores the importance of rigorous verification and cross-referencing when evaluating claims made by purported hackers or leak sellers. It also highlights how geopolitical events can be exploited by bad actors to gain credibility in underground forums.
As I always appreciate sharing data in our field, I must say they analysis of Sam Bent, in this case, seems to be wrong:
Source: https://doingfedtime.com/kavim-data-leak-29-000-records-compromised/