China’s New Weapon: SMS Phishing at Scale AKA U.S. toll road smishing scams.
Smishing-as-a-Service is the new startup no one asked for—scaling faster than your favorite SaaS.
China’s New Weapon: SMS Phishing at Scale
While the world obsesses over advanced malware, zero-day exploits, and AI-driven reconnaissance tools, a new report reminds us that sometimes, low-tech attacks, executed at scale, can be just as devastating. Cybersecurity researchers have uncovered a China-linked smishing-as-a-service (SaaS) kit that’s being used in widespread campaigns targeting mobile users across telecom networks in Europe, Asia, and North America.
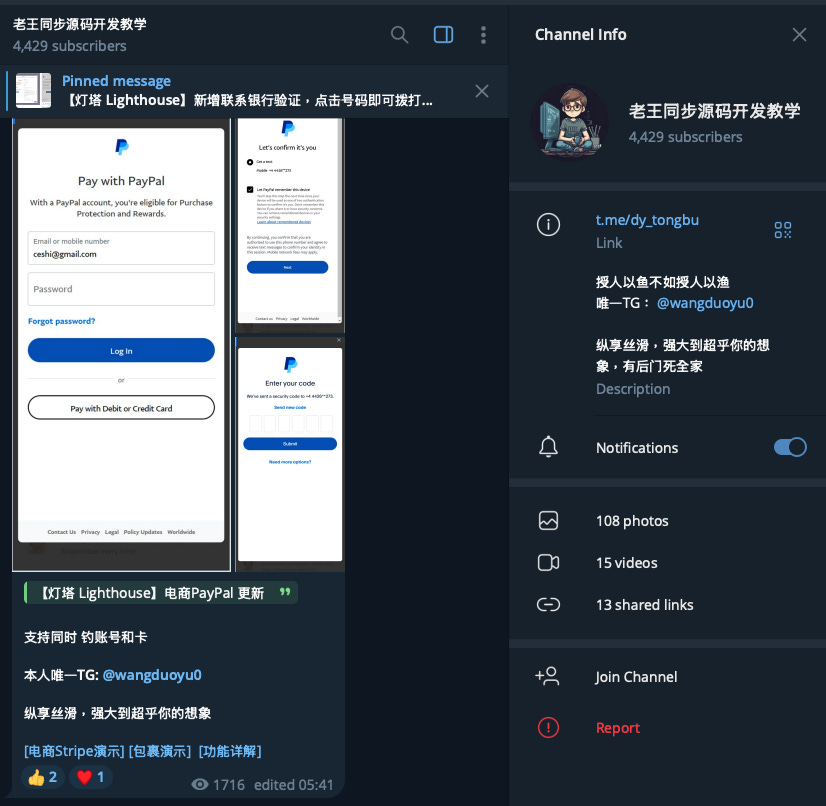
This isn’t the usual poorly-written scam. What we’re dealing with is a professionally developed infrastructure, designed to harvest credentials, session cookies, OTP codes, and forward them in real time to attacker-controlled Telegram bots.
This kit transforms phishing from a manual effort to a fully automated business model. It’s fast. It’s scalable. And it’s frighteningly effective.
How It Works: Simplicity with Speed
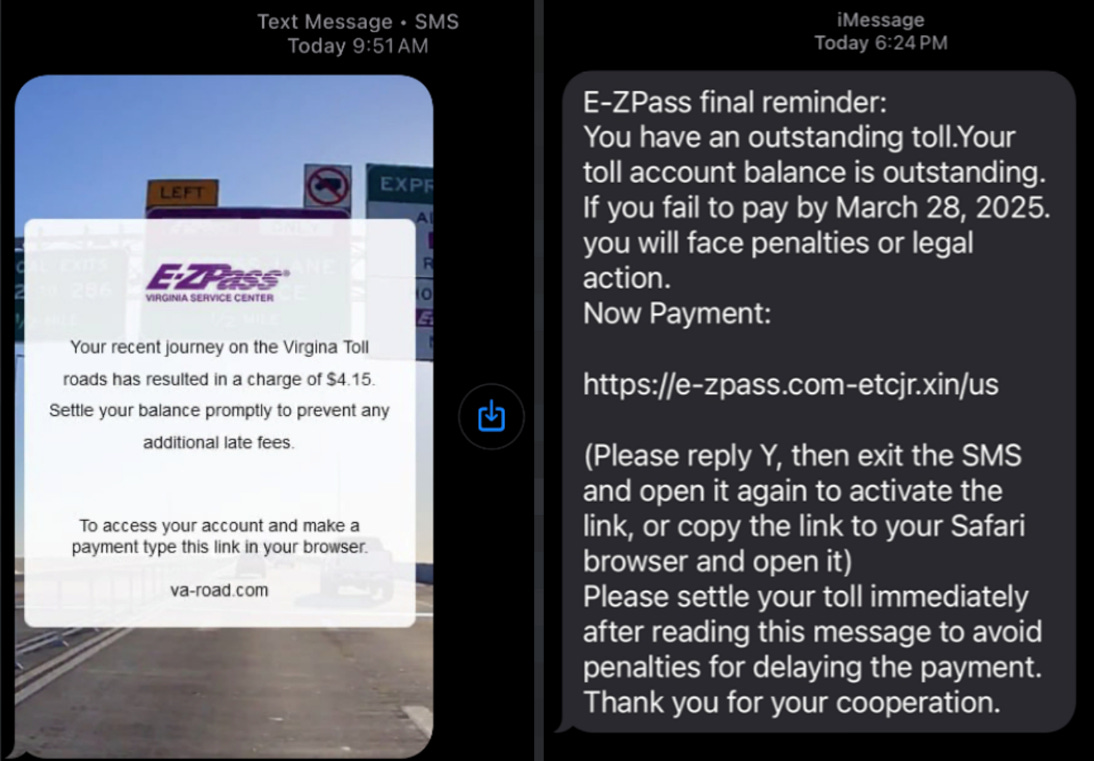
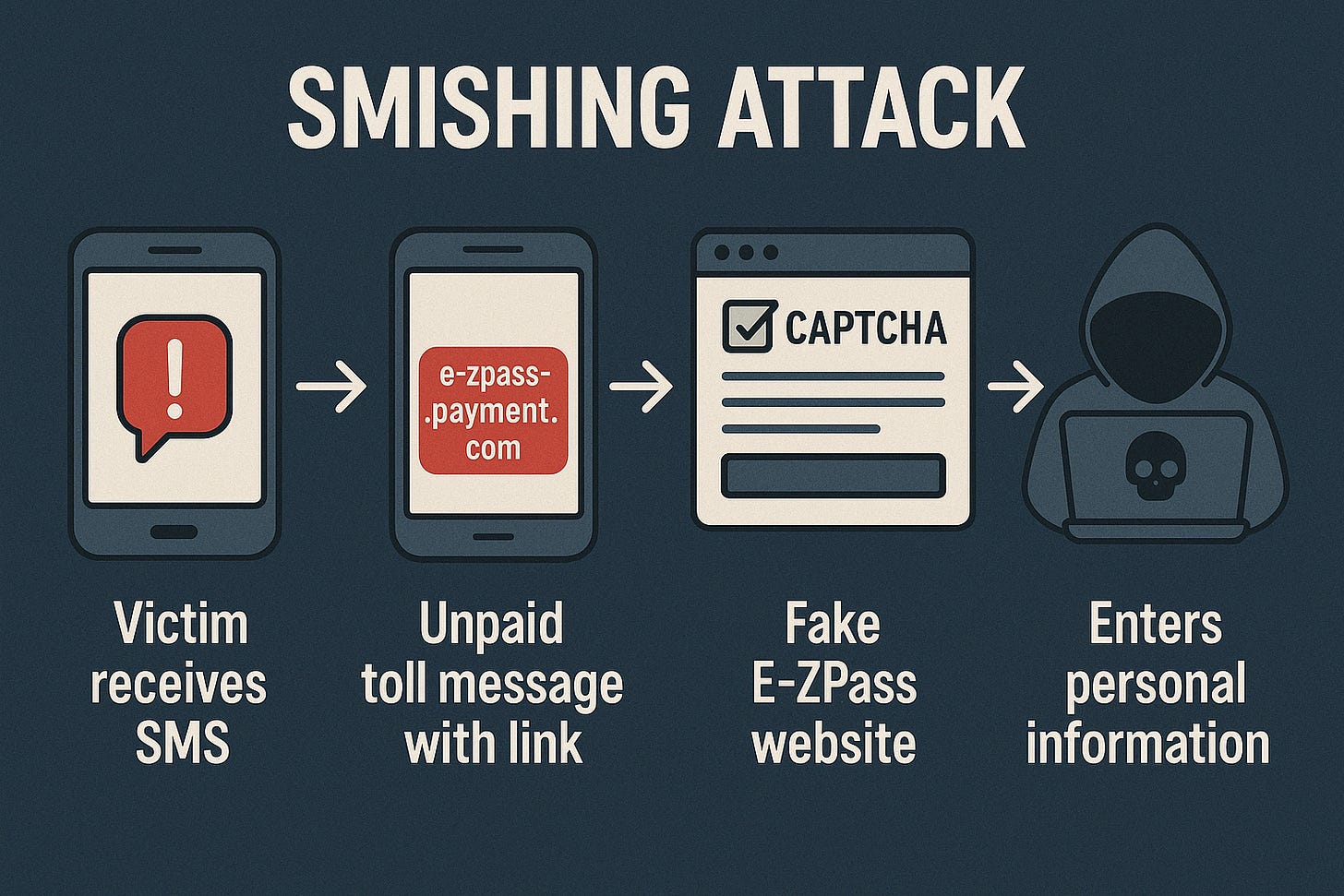
The attack begins with a single SMS message—clean, localized, and believable. It might impersonate your telecom provider, a delivery service, or your bank. The link inside redirects to a phishing page that’s been tailored to mimic the mobile site of the spoofed brand with near-pixel perfection.
As soon as the victim enters their information—be it login credentials, PINs, or verification codes—the data is forwarded immediately to the attacker's bot. No delays. No time to second-guess.
The result? In many cases, attackers are able to bypass MFA protections before the user even realizes they’ve been compromised. Real-time relay means the attack window is small, but lethal.
Infrastructure: Mass-Produced Deception
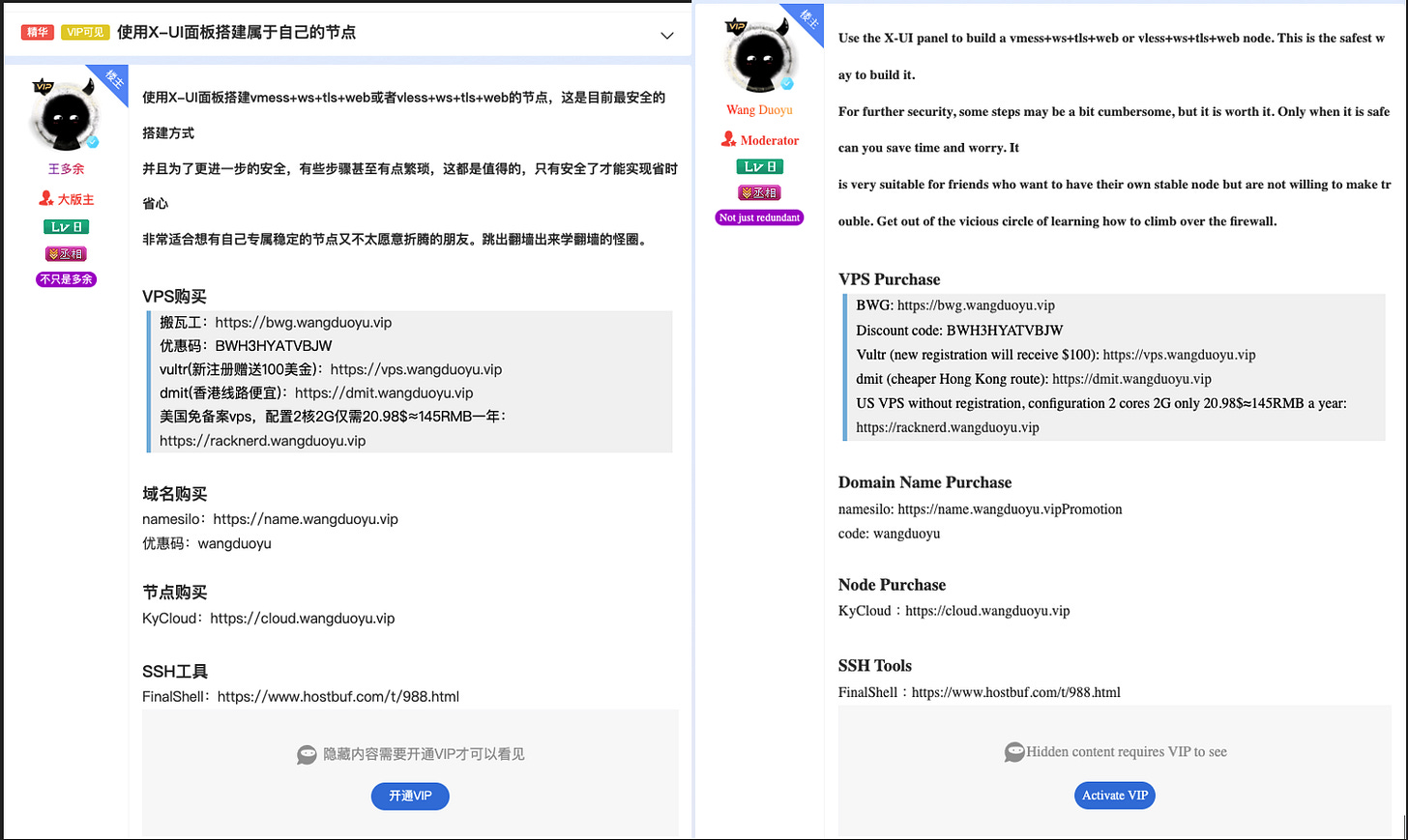
The kit includes:
Dozens of pre-built phishing templates for common targets (banks, telcos, couriers)
Real-time Telegram bot integration for automated credential forwarding
Dynamic URL generation to evade filters and domain blacklists
Hosting rotation scripts to keep infrastructure one step ahead of takedowns
In essence, it offers turnkey cybercrime. Even low-skilled threat actors can now run sophisticated smishing campaigns that rival state-level operations in speed and efficacy.
The kit’s infrastructure is being repurposed in campaigns that impersonate legitimate U.S. entities like toll road services, drawing unsuspecting victims into fake payment portals. The messages are short, urgent, and geographically personalized, which makes them especially convincing.
Researchers also noted the use of link shortening services, redirection layers, and geographic IP filtering to further obfuscate detection and maximize victim engagement.
Researchers discovered monetization features embedded into the kit—meaning its creators have a secondary revenue stream by selling stolen credentials on the dark web, in addition to providing "smishing kits for hire."
Attribution: A Familiar Shadow
The smishing kit contains language artifacts, Telegram handles, and behavioral patterns that strongly suggest a Chinese-speaking developer or group. This actor has been previously tied to:
SIM-swapping crews
Credential stuffing operations
Dark web marketplaces selling telecom logins and OTP bypass methods
Although the motive here appears financial, the implications are geopolitical. Stolen telecom credentials can be a gateway to espionage-grade intelligence. Imagine the value of gaining access to accounts tied to government employees, executives, or infrastructure engineers.
Global Targeting, Local Deception
The key to this campaign’s success is localization. Each phishing template is tailored to:
Match the language and branding of regional telecom operators
Use regional SMS sender IDs to appear legitimate
Evade detection by anti-spam filters that rely on global indicators
This regional customization leads to exponentially higher click-through and credential submission rates.
Researchers also observed that the actors use domain names closely resembling the original entities (e.g., misspelled toll road names, slight alterations to domain suffixes) which add credibility at a glance and evade common filter logic.
What You Can Do
For Security Teams:
Implement anomaly detection for real-time token use and rapid credential changes
Use threat intelligence feeds to block known Telegram bot endpoints and phishing domains
Deploy SMS firewalls to inspect and block malicious message patterns
Monitor for domain spoofing or look-alike domains registered in bulk
For Users:
Never click links from unknown senders—even if the message appears urgent or legitimate
Use official apps instead of browser-based logins
Report suspicious SMS messages to your mobile provider or national CERT
Be especially cautious with messages involving toll payments, banking updates, or delivery confirmations
This isn’t just another phishing campaign—it’s a mass production engine for mobile compromise. The combination of real-time exfiltration, bot automation, and localized deception makes this threat one of the most operationally advanced smishing campaigns we’ve seen to date.
The tech is simple. The execution is not.