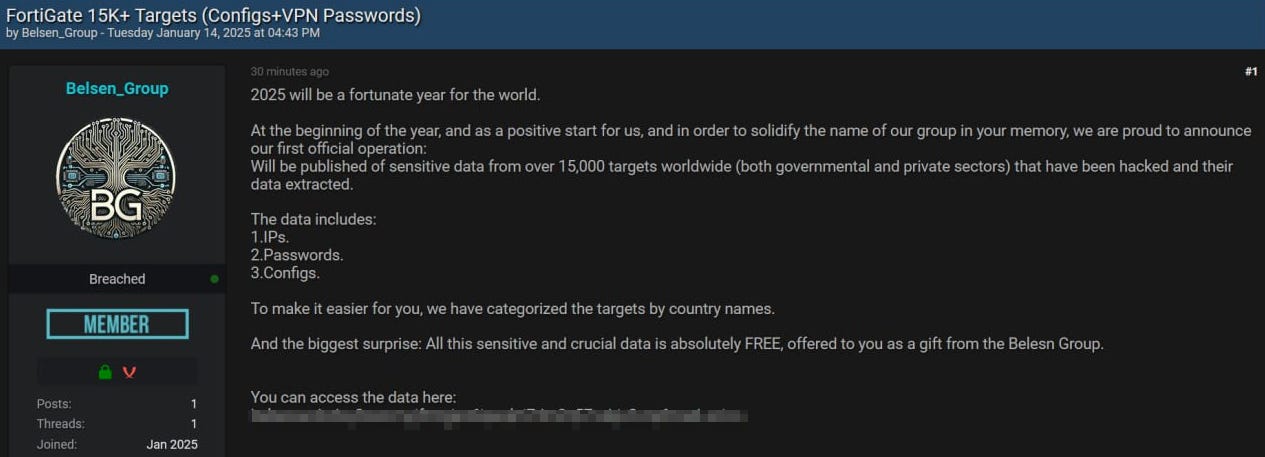
Belsen Group just dropped 15,000 FortiGate targets on BreachForums.
In a bold start to 2025, the hacking collective known as the Belsen Group has made waves on BreachedForums by releasing over 15,000 FortiGate targets, including sensitive configurations, IPs, and PW's
Belsen Group has kicked off 2025 with a cyberattack that sends shockwaves through the global cybersecurity community. On the infamous BreachedForums, the group announced their acquisition of sensitive data from over 15,000 Fortigate devices worldwide. The leaked data, categorized by country, includes full configuration dumps and VPN password files. What’s more, this trove of information is being offered completely free, signaling a bold and potentially catastrophic cyber incident.
What Happened?
A ZIP file shared by the Belsen Group contains folders for each targeted IP address. Inside each folder are two critical files:
config.conf – A full configuration dump of the Fortigate device.
vpn-passwords.txt – Sensitive VPN access credentials.
Analysis reveals that the leaked data likely originates from Fortigate 7.x and 7.2.x devices, hinting at a potential zero-day exploit in Fortinet’s latest firmware. Some of the IP addresses even align with Shodan, a search engine for internet-connected devices, suggesting targeted reconnaissance was employed to identify these systems.
The legitimacy of the data is supported by the unique configurations and the alignment of these devices to Shodan queries, demonstrating a calculated and effective breach.
Why This Matters
The scale of this breach, affecting over 15,000 devices in both governmental and private sectors, underscores the severity of the attack. Here’s why it poses a significant threat:
Network Compromise: With access to configuration files and VPN passwords, attackers could infiltrate sensitive networks undetected.
Zero-Day Exploit: The possibility of an unreported Fortigate vulnerability means thousands of organizations worldwide are at immediate risk.
Supply Chain Implications: Breached Fortigate devices could serve as entry points for further attacks, compromising entire ecosystems.
The Bigger Picture
This incident is another example of threat actors exploiting overlooked or undisclosed vulnerabilities in widely used systems. Fortinet devices are staples in the cybersecurity infrastructure of countless organizations, and a breach of this magnitude undermines trust in critical systems.
The Belsen Group’s audacity to release the data for free adds a layer of chaos to the event. While some see it as an act of defiance, it’s clear that this move was designed to attract attention, disrupt systems, and erode confidence in cybersecurity standards.
The Bottom Line
This is a wake-up call for organizations relying on Fortinet products. Immediate actions to mitigate risks include:
Audit and Update: Ensure devices are running the latest firmware versions, and review configurations for vulnerabilities.
Change Credentials: Update all VPN credentials as a precaution.
Monitor Traffic: Proactively monitor for unauthorized access or unusual network behavior.
The Belsen Group has made a bold statement, but this is far from the end of the story. The incident demonstrates that no organization, no matter how robust its security measures, is immune to determined threat actors.
P.S