0-Day Drops: The 7-Zip Vulnerability Exploit Goes Public
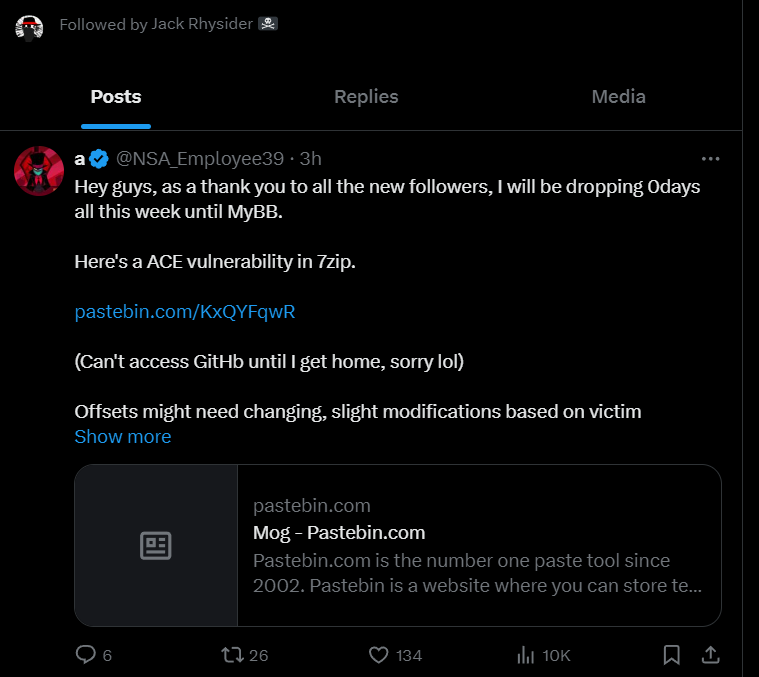
A storm is brewing in the cybersecurity world as @NSA_Employee39, a controversial figure with a growing following on X (formerly Twitter), leaks an 0-day exploit targeting 7-Zip.
The Exploit at a Glance
What it does: The exploit manipulates a buffer overflow in the LZMA stream decoder of 7-Zip, allowing attackers to execute arbitrary code. A seemingly harmless .7z file could trigger this exploit when opened, delivering a payload like launching
calc.exe—or worse.How it works: It leverages malformed streams to tamper with internal buffer pointers, creating an opening for shellcode execution. With some adjustments to offsets, attackers can tailor it to specific targets.
Impact: If successfully exploited, this vulnerability could allow attackers to take complete control of a victim's system, putting businesses, individuals, and even critical infrastructure at risk.
The Role of @NSA_Employee39
This isn’t the first time @NSA_Employee39 has stirred controversy on X. Known for sharing exploit code and vulnerability disclosures, their account has become a magnet for both aspiring hackers and concerned cybersecurity professionals. Their followers have grown rapidly in the wake of these leaks, and their posts often spark heated debates about the ethics of public exploit disclosure.
Key highlights from the X post:
A Pastebin link to the exploit, openly shared with followers.
Mentions of further 0-day drops planned for the week, keeping the community on edge.
What’s the Bigger Picture?
This leak is part of a broader trend of 0-day vulnerabilities being dropped publicly. While some see this as irresponsible, others argue that exposing these exploits forces vendors to act quickly to secure their software.
Key concerns:
Attackers’ playground: Threat actors now have an advanced exploit at their disposal, potentially increasing attacks against unpatched 7-Zip versions.
Wider reach: 7-Zip is used globally, from enterprise environments to individual users, making this a high-impact vulnerability.
Ethics of disclosure: The public nature of @NSA_Employee39’s post reignites debates over whether such leaks do more harm than good.
Why It Matters
The release of this exploit highlights several pressing issues in cybersecurity:
Patch urgency: If you’re using 7-Zip, update to the latest version immediately—or risk being an easy target.
Public vs. private disclosure: The ethics of dropping exploits publicly without prior vendor notification remain hotly debated.
Influence of X profiles: The platform is becoming a significant hub for exploit releases, bringing both awareness and chaos to the cybersecurity space.
What Should You Do?
Update your software: Check for the latest version of 7-Zip and apply updates immediately.
Audit your environment: Review where 7-Zip is used in your organization and consider alternatives for critical workflows.
Monitor for threats: Security teams should look for indicators of exploitation targeting this vulnerability.
This latest 0-day drop is a sobering reminder of the fragility of our digital tools—and the chaos that can unfold when they’re exploited. Platforms like X are proving to be double-edged swords: a space for knowledge sharing and a battlefield for cyber vulnerabilities.